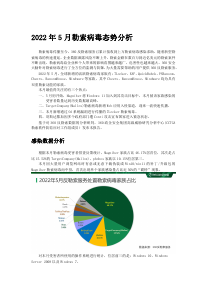
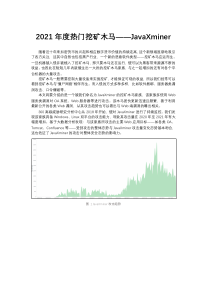
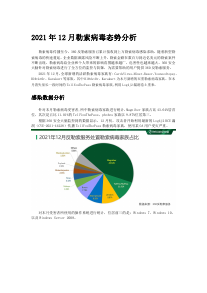
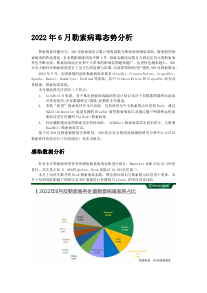
11.01.2023 | kaspersky.com

Threat landscape for industrial automation systems
20.05.2022 | kaspersky.com

ISaPWN – research on the security of ISaGRAF Runtime
| blackhat.com

Microsoft Word - eu-20-Clarke-Its-Not-FINished-The-Evolving-Maturity-In-Ransomware-Operations-wp.docx
25.03.2022 | trendmicro.com

A Look Into Purple Fox’s New Arrival Vector
22.07.2016 | ptsecurity.com

SECURITY TRENDS & VULNERABILITIES REVIEW
29.09.2015 | recordedfuture.com

Proactive Threat Identification Neutralizes Remote Access Trojan Efficacy
| recordedfuture.com

North Korea Targeted South Korean Cryptocurrency Users and Exchange in Late 2017 Campaign
21.10.2022 | recordedfuture.com

Recorded Future 인텔리전스 플랫폼의 Total Economic Impact
01.04.2015 | trendmicro.com

A Profile of IRS Scammers: Behind Tax Fraud
13.11.2014 | trendmicro.com

The Brazilian Underground Market: The Market for Cybercriminal Wannabes?
01.09.2021 | ptsecurity.com

Information security risks at industrial companies
14.11.2017 | recordedfuture.com

Ministry of National State Network Security Likely China’s Influences Vulnerability Publications
09.06.2020 | 360.cn

Windows 10 20H1.19577 开始 System 进程内 Ntdll 的一点变化
06.12.2023 | microsoft.com

Microsoft Security Compliance and Identity
05.05.2021 | europa.eu

Insufficient Access Control Vulnerability in the Dell Driver
12.09.2019 | trendmicro.com

Hacking LED Wristbands as a Learning Opportunity to Jump on RF Security
12.01.2021 | bitdefender.com

Macintosh HD:Users:Shared:dd:4work:Bitdefender-PR-Whitepaper-Remcos-creat5080-en_EN:Bitdefender-PR-Whitepaper-Remcos-creat5080-en_EN.indd
13.09.2016 | proofpoint.com

Splunk Integration with Proofpoint Threat Response and ET Intelligence
29.04.2024 | bitdefender.com

Bitdefender-Report-Confidential-DeepDive-creat7721-en_EN
09.10.2018 | recordedfuture.com

Thieves and Geeks: Russian and Chinese Hacking Communities
03.12.2018 | recordedfuture.com

Underlying Dimensions of Yemen’s Civil War: Control of the Internet
18.10.2023 | recordedfuture.com

Russia Creates No-Win Situation for Western Companies
01.06.2018 | spectreattack.com

Spectre Attacks: Exploiting Speculative Execution
03.10.2018 | thecssc.com

Indicators of Compromise for Malware used by APT28
14.02.2014 | trendmicro.com

Point-of-Sale System Breaches: Threats to the Retail and Hospitality Industries
26.06.2018 | recordedfuture.com

RedAlpha: New Campaigns Discovered Targeting the Tibetan Community
06.06.2018 | recordedfuture.com

North Korea Relies on American Technology for Internet Operations
15.03.2016 | proofpoint.com